Quality isn’t just about functionality anymore – security has become a critical pillar of software quality. Today, I want to share how I’m diving into security testing for web application projects using popular tools like Burp Suite, ZAP (Zed Attack Proxy), and Kali Linux.
Recently, I’ve been exploring security testing, and it completely changed how I view quality assurance. I realized that security isn’t just a specialist’s profession – it’s something we all need to be thinking about, especially as part of a shift-left QA strategy.
As a QA Engineer, my primary focus has always been on functionality, reliability, and performance. But the more I’ve explored security testing, the more I’ve realized how crucial it is for every tester – not just security pros—to understand and adopt a security-first mindset in our testing efforts.
Most security-related content out there either scratches the surface or dives too deep into the realm of ethical hacking. So let’s bridge that gap—beyond the basics, beyond the buzzwords—and explore how you can integrate security into your everyday QA process.
In some of companies, security testing is not applied extensively in software projects. One major reason is that it demands dedicated resources, need a manpower professionals, and often increases project costs. Unlike functional testing, security testing involves ethical hacking, vulnerability scanning, and deep technical analysis—tasks that may require specialized tools and experienced security testers.
What Is Security Testing?
One of the most important goals of security testing is to verify that your web application is not open to attack via any vulnerabilities. That is to say, the purpose of security testing is to ensure your application can resist such malicious activities as SQL injections (i. e. the modification of database query statements using special characters), XSS (Cross-site Scripting), unauthorized access and so on.
Instead of going straight for your testing tools, it is best to first understand the basics of conducting methodical security analysis in the environment for which you have built a development project.
🌐 Detecting Hosting IP Address and Basic Information
Before start testing, it’s important to understand how attackers identify potential targets. In security testing, the first step is often gathering information about specific application. Here’s how you can get started:
🔍 Find the Hosting IP Address
There are many tools you can use to find out where your web application is hosted and gather other valuable data. For example:
- Use
nslookupordig(Command-line tools)- These tools can help you find the IP address of the domain.
- Example
nslookup example.com
- Use online services like https://www.whatismyip.com
- They help you trace the location of your IP and verify if it’s publicly exposed. or else, use the chrome extension to capture the DNS server.
🖥️ WHOIS Lookup
You can also perform a WHOIS lookup to get more information about the domain owner, registrar, and hosting details. This gives you clues about the server location and provider.
🧪 Security Testing Method
Now, once analyze information and after that we have the basic information, let’s talk about the approach to performing security testing.
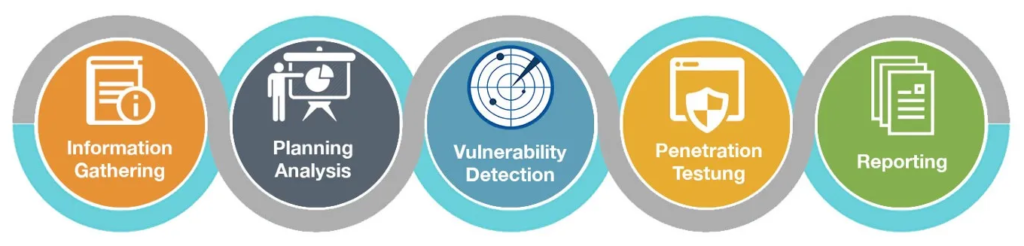
- Step 1: Reconnaissance
Start by performing passive reconnaissance—gathering all publicly available data without interacting directly with the target application. You can use online tools, WHOIS data, and open-source intelligence (OSINT) methods to gather insights about the app and its hosting infrastructure.
- Step 2: Scanning
Next, use scanning tools to identify common vulnerabilities in the application. This includes things like port scanning, server fingerprinting, and identifying misconfigurations.
- Step 3: Attacking
Once vulnerabilities are found, it’s time to simulate attacks to check if the web application is vulnerable to them. Use tools like Burp Suite or ZAP to launch and analyze attacks like SQL injections, XSS, or XXE.
Practical Attack Methods
Here’s how we can conduct some of the most common attacks:
1. SQL Injection (SQLi)
SQL Injection happens when an application allows an attacker to inject SQL code via an input field (e.g., search bar or login form).
- How to Test for SQLi:
- Enter a string like
admin' --or1' OR '1'='1into form fields. - If the application returns an error or behaves unexpectedly, it may be vulnerable.
- Enter a string like
- Tools:
- Burp Suite Intruder: Use this tool to automate SQLi payload injection.
- Burp Suite Intruder: Use this tool to automate SQLi payload injection.
2. Cross-Site Scripting (XSS)
XSS happens when attackers inject malicious scripts into web pages that are then executed in a user’s browser.
- How to Test for XSS:
- Inject a payload like
<script>alert('XSS')</script>into a form or URL parameter. - If an alert box appears or your script is executed, the site is vulnerable.
- Inject a payload like
- Tools:
- Burp Suite and ZAP can help you intercept and test inputs for potential XSS vulnerabilities.
- Burp Suite and ZAP can help you intercept and test inputs for potential XSS vulnerabilities.
3. XXE (XML External Entity Injection)
XXE occurs when an attacker can send malicious XML input to an application that parses XML files.
- How to Test for XXE:
- Send a crafted XML payload that attempts to read files from the system (e.g.,
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>). - Observe if the server returns sensitive data.
- Send a crafted XML payload that attempts to read files from the system (e.g.,
- Tools:
- Burp Suite: Use its Intruder tool for automated XXE injection.
- Burp Suite: Use its Intruder tool for automated XXE injection.
Tools for Security Testing
01. Burp Suite (Community Edition)
Burp Suite is a powerful interception proxy tool for web app testing. I highly recommend exploring the PortSwigger Academy – it’s free and hands-on.
https://portswigger.net/web-security
Steps:
- Set up Burp Suite Community Edition.
- Configure browser to use Burp Proxy (127.0.0.1:8080).
- Intercept a login request from your app.
- Modify parameters to test for XSS/SQLi.
- Analyze responses and behavior.
02. ZAP – Zed Attack Proxy
ZAP is an open-source alternative to Burp. It’s beginner-friendly and works great for automated vulnerability scanning.
- Download & launch ZAP.
- Set up your browser to route traffic through ZAP.
- Run an active scan on your app.
- Review alerts for vulnerabilities.
03. Nikto
Scan your web site and server immediately with the popular Nikto Web Scanner. This testing service can be used to test a Web Site, Virtual Host and Web Server for known security vulnerabilities and mis-configurations.
https://github.com/sullo/nikto
04. Metasploit Framework
- Purpose: Web app scanner and attack tool
- Use Case: Identify and exploit web vulnerabilities
- Link: https://github.com/andresriancho/w3af
Using Kali Linux
Kali Linux is a penetration testing Linux distribution packed with security tools. Also, designed for penetration testing and ethical hacking. It includes tools like Nikto, Nmap, Metasploit, and SQLMap.
- Download and run Kali in a VM (like VirtualBox).
- Use tools like Nikto, Nmap, and SQLMap.
- real-world attacks like brute force, port scanning, etc.
- Target your application in a controlled test environment.
⚠️ Note: Never test in production. Always test in local/staging environments.
Why QA Engineers Should Learn Security Testing
As a QA Engineer, your role is evolving. Understanding and implementing security testing not only strengthens your skills but ensures the overall security of the product you’re testing. You can be a critical part of the development team, helping to prevent data breaches, unauthorized access, and other vulnerabilities from affecting users.